Key Offering
Enabler of Effective Data Management through the use of web-enabler system
Enterprise Data Management Model


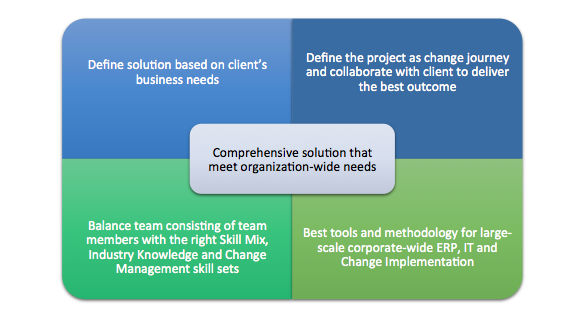
Project & Change Management
Defence & Security Assessment
To verify the security of the installed system chain and to perform a mapping of the major security vulnerabilities of deployed infrastructure based of the latest domain knowledge and state-of-art
Security Tests Capabilities
- Test lab helps to validate that security measures have been implemented correctly.
- Recommends an approach based on security requirements for component testing.
- Test on complete systems in live-like scenarios.
- Penetration tests can be performed on operational systems
Step 1
- Information Intake and Preparation
Step 2
- Lab Test Execution
Step 3
- Onsite Test Execution
Step 4
- Development of Secure Target State Architecture
Step 5
- Test Report Creation & Workshop